Anthem
Exploit a Windows machine in this beginner-level challenge.
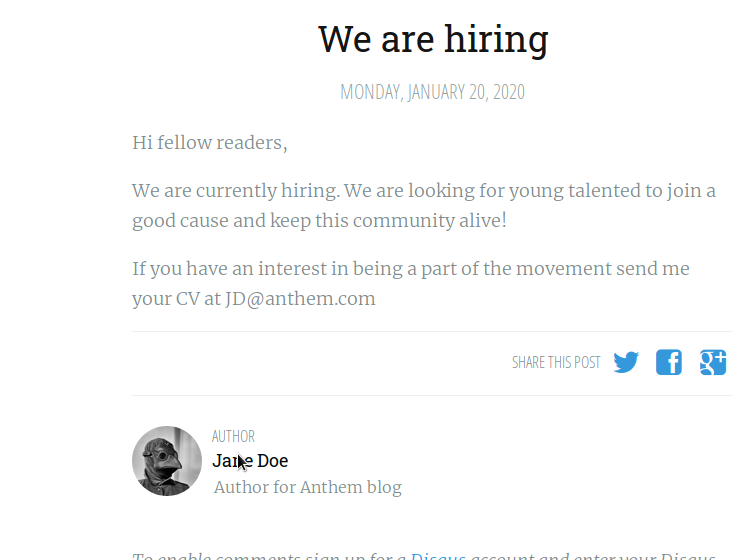
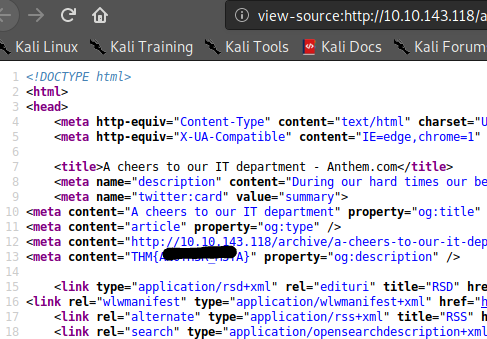
We first did a Nmap scan to check information about services and open ports.
Nmap scan result:
Starting Nmap 7.80 ( https://nmap.org ) at 2020-05-31 15:29 UTC
NSE: Loaded 151 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 15:29
Completed NSE at 15:29, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 15:29
Completed NSE at 15:29, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 15:29
Completed NSE at 15:29, 0.00s elapsed
Initiating Ping Scan at 15:29
Scanning 10.10.143.118 [4 ports]
Completed Ping Scan at 15:29, 2.18s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 15:29
Completed Parallel DNS resolution of 1 host. at 15:29, 0.02s elapsed
Initiating SYN Stealth Scan at 15:29
Scanning 10.10.143.118 [1000 ports]
Discovered open port 80/tcp on 10.10.143.118
Discovered open port 135/tcp on 10.10.143.118
Discovered open port 445/tcp on 10.10.143.118
Discovered open port 3389/tcp on 10.10.143.118
Discovered open port 139/tcp on 10.10.143.118
Increasing send delay for 10.10.143.118 from 0 to 5 due to 141 out of 469 dropped probes since last increase.
Completed SYN Stealth Scan at 15:30, 17.74s elapsed (1000 total ports)
Initiating Service scan at 15:30
Scanning 5 services on 10.10.143.118
Completed Service scan at 15:30, 16.71s elapsed (5 services on 1 host)
Initiating OS detection (try #1) against 10.10.143.118
Retrying OS detection (try #2) against 10.10.143.118
Retrying OS detection (try #3) against 10.10.143.118
Retrying OS detection (try #4) against 10.10.143.118
Retrying OS detection (try #5) against 10.10.143.118
Initiating Traceroute at 15:30
Completed Traceroute at 15:30, 0.15s elapsed
Initiating Parallel DNS resolution of 2 hosts. at 15:30
Completed Parallel DNS resolution of 2 hosts. at 15:30, 0.00s elapsed
NSE: Script scanning 10.10.143.118.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 15:30
NSE Timing: About 99.10% done; ETC: 15:31 (0:00:00 remaining)
Completed NSE at 15:31, 44.02s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 15:31
Completed NSE at 15:31, 0.99s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 15:31
Completed NSE at 15:31, 0.00s elapsed
Nmap scan report for 10.10.143.118
The host is up, received timestamp-reply TTL 127 (0.16s latency).
Scanned at 2020-05-31 15:29:45 UTC for 93s
Not shown: 995 closed ports
Reason: 995 resets
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
| HTTP-methods:
|_ Supported Methods: OPTIONS
135/tcp open msrpc syn-ack TTL 127 Microsoft Windows RPC
139/tcp open NetBIOS-ssn syn-ack TTL 127 Microsoft Windows NetBIOS-ssn
445/tcp open Microsoft-ds? syn-ack TTL 127
3389/tcp open ms-web-server syn-ack TTL 127 Microsoft Terminal Services
| RDP-ntlm-info:
| Target_Name: WIN-LU09299160F
| NetBIOS_Domain_Name: WIN-LU09299160F
| NetBIOS_Computer_Name: WIN-LU09299160F
| DNS_Domain_Name: WIN-LU09299160F
| DNS_Computer_Name: WIN-LU09299160F
| Product_Version: 10.0.17763
|_ System_Time: 2020-05-31T15:30:39+00:00 ssl-cert: Subject: commonName=WIN-LU09299160F
| Issuer: commonName=WIN-LU09299160F
| Public Key type: RSA
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2020-04-04T22:56:38
| Not valid after: 2020-10-04T22:56:38
| MD5: 2814 61de 95b7 e9b5 4789 3027 7f1f 60d2
| SHA-1: d47d 2a8f 6143 b820 936e 4120 cdd1 9ddc 5385 d285
| -----BEGIN CERTIFICATE-----
| MIIC4jCCAcqgAwIBAgIQObhN9c8QnIVGx+ZslzEOmzANBgkqhkiG9w0BAQsFADAa
| MRgwFgYDVQQDEw9XSU4tTFUwOTI5OTE2MEYwHhcNMjAwNDA0MjI1NjM4WhcNMjAx
| MDA0MjI1NjM4WjAaMRgwFgYDVQQDEw9XSU4tTFUwOTI5OTE2MEYwggEiMA0GCSqG
| SIb3DQEBAQUAA4IBDwAwggEKAoIBAQDA4MPIi4yCYJlBv6vwXF5lu5NbQCPQxk4q
| 7lJsJSvTRSIFi2fVl3l+rWTr69mutnVqo+bMilJorN2B6DqsCJBV+7pITFSICM6b
| +G/sOEblVust2tUU8NLbAiBH9oXhF0P5dIhMzRC4pcZjhCRR+IcOjnABTCkdAchD
| Mf4XQJx6GZOXBCBMXGW/vCKZ0q8gti7Hxs36W1ctbj8/i5obd0k0BonMlvRwKxvi
| 7SS+3NrBpc4XivD23YIqCNzErOB19DV3JqZMvbE+NhLEQA51Au2svYwgoJcIIyEC
| HBuINXeFBB+p5dMwp4wppkHN0CuquUyCBZvIPlDW8SAOAc5tgUOJAgMBAAGjJDAi
| MBMGA1UdJQQMMAoGCCsGAQUFBwMBMAsGA1UdDwQEAwIEMDANBgkqhkiG9w0BAQsF
| AAOCAQEAAziR6P3nN9/EKLhZqJKgkWP9FyNr9CusD78wem1C5fn9h7SjS1PQEhn1
| Gi50rlcUmII4E8Bnv6g/1QZnZIsPtVzO3bokQfbhTEzWOQ8RScB3ZQ+Tg7xM4duA
| NZdzR1/hjOOmPBV4ih3+AKmbEZ63V3PuJOn2+0/NsGXzGKhaNhlAof58lXkXrt9x
| DvmpyfER7oq/3+kPQhXlNK7VZ/dp26BLFQT12be1yyeVck2n/90pXTxV/COaIdsF
| q7RJPVO+4FCua77sUUSV9E5CL3oOFJT5MjkAMEkoKsU9InWHhA5w+ndQqDgXIb40
| 7b3pD6AiS/ZEvSpzCyeVnDprZxVIaQ==
|_-----END CERTIFICATE-----
|_ssl-date: 2020-05-31T15:31:23+00:00; +5s from scanner time.
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.80%E=4%D=5/31%OT=80%CT=1%CU=36494%PV=Y%DS=2%DC=T%G=Y%TM=5ED3CDC
OS:7%P=x86_64-pc-linux-gnu)SEQ(SP=107%GCD=1%ISR=10C%TI=I%CI=I%II=I%SS=S%TS=
OS: U)OPS(O1=M472NW8NNS%O2=M472NW8NNS%O3=M472NW8%O4=M472NW8NNS%O5=M472NW8NNS
OS:%O6=M472NNS)WIN(W1=FFFF%W2=FFFF%W3=FFFF%W4=FFFF%W5=FFFF%W6=FF70)ECN(R=Y%
OS:DF=Y%T=80%W=FFFF%O=M472NW8NNS%CC=Y%Q=)T1(R=Y%DF=Y%T=80%S=O%A=S+%F=AS%RD=
OS:0%Q=)T2(R=Y%DF=Y%T=80%W=0%S=Z%A=S%F=AR%O=%RD=0%Q=)T3(R=Y%DF=Y%T=80%W=0%S
OS:=Z%A=O%F=AR%O=%RD=0%Q=)T4(R=Y%DF=Y%T=80%W=0%S=A%A=O%F=R%O=%RD=0%Q=)T5(R=
OS:Y%DF=Y%T=80%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=80%W=0%S=A%A=O%F=
OS:R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=80%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T
OS:=80%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=80%CD=
OS: Z)
Network Distance: 2 hops
TCP Sequence Prediction: Difficulty=263 (Good luck!)
IP ID Sequence Generation: Incremental
Service Info: OS: Windows; CPE: CPE:/o:Microsoft: windows
Host script results:
|_clock-skew: mean: 4s, deviation: 0s, median: 4s
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 63696/tcp): CLEAN (Couldn't connect)
| Check 2 (port 9759/tcp): CLEAN (Couldn't connect)
| Check 3 (port 11484/udp): CLEAN (Timeout)
| Check 4 (port 40612/udp): CLEAN (Failed to receive data)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2020-05-31T15:30:41
|_ start_date: N/A
TRACEROUTE (using port 111/tcp)
HOP RTT ADDRESS
1 149.26 ms 10.9.0.1
2 149.36 ms 10.10.143.118
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 3) scan.
Initiating NSE at 15:31
Completed NSE at 15:31, 0.00s elapsed
NSE: Starting runlevel 2 (of 3) scan.
Initiating NSE at 15:31
Completed NSE at 15:31, 0.00s elapsed
NSE: Starting runlevel 3 (of 3) scan.
Initiating NSE at 15:31
Completed NSE at 15:31, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/.
Nmap did: 1 IP address (1 host up) scanned in 95.87 seconds
Raw packets sent: 1802 (82.810KB) | Rcvd: 1122 (48.122KB)
 |




















0 Comments