Basic Pentesting 1 covers all basic parts like Linux enumeration, hash cracking, brute-forcing through Hydra, and privilege escalation.
So let's start with Nmap scan:
kali@kali:~$ Sudo Nmap -sV -O -A 10.10.252.119
Starting Nmap 7.80 ( https://nmap.org ) at 2020-05-29 06:00 UTC
Nmap scan report for 10.10.252.119
The host is up (0.21s latency).
Not shown: 996 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 db:45:cb:be:4a:8b:71:f8:e9:31:42:ae:ff:f8:45:e4 (RSA)
| 256 09:b9:b9:1c:e0:bf:0e:1c:6f:7f:fe:8e:5f:20:1b:ce (ECDSA)
|_ 256 a5:68:2b:22:5f:98:4a:62:21:3d:a2:e2:c5:a9:f7:c2 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.80%E=4%D=5/29%OT=22%CT=1%CU=32267%PV=Y%DS=2%DC=T%G=Y%TM=5ED0A56
OS:B%P=x86_64-pc-linux-gnu)SEQ(SP=106%GCD=1%ISR=10A%TI=Z%TS=B)SEQ(SP=EC%GCD
OS:=1%ISR=FE%TI=Z%CI=I%II=I%TS=A)SEQ(CI=RD%TS=8)SEQ(SP=105%GCD=1%ISR=107%TI
OS:=Z%CI=I%TS=C)OPS(O1=M508ST11NW6%O2=M508ST11NW6%O3=M508NNT11NW6%O4=M508ST
OS:11NW6%O5=M508ST11NW6%O6=M508ST11)WIN(W1=68DF%W2=68DF%W3=68DF%W4=68DF%W5=
OS:68DF%W6=68DF)ECN(R=Y%DF=Y%T=40%W=6903%O=M508NNSNW6%CC=Y%Q=)T1(R=Y%DF=Y%T
OS:=40%S=O%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R
OS:%O=%RD=0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=
OS:40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0
OS:%Q=)U1(R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R
OS:=Y%DFI=N%T=40%CD=S)
Network Distance: 2 hops
Service Info: Host: BASIC2; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: 1h20m03s, deviation: 2h18m35s, median: 2s
|_nbstat: NetBIOS name: BASIC2, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
| Computer name: basic2
| NetBIOS computer name: BASIC2\x00
| Domain name: \x00
| FQDN: basic2
|_ System time: 2020-05-29T02:02:00-04:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2020-05-29T06:02:01
|_ start_date: N/A
TRACEROUTE (using port 993/tcp)
HOP RTT ADDRESS
1 242.08 ms 10.9.0.1
2 242.12 ms 10.10.252.119
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap did: 1 IP address (1 host up) scanned in 90.66 seconds
Starting Nmap 7.80 ( https://nmap.org ) at 2020-05-29 06:00 UTC
Nmap scan report for 10.10.252.119
The host is up (0.21s latency).
Not shown: 996 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 db:45:cb:be:4a:8b:71:f8:e9:31:42:ae:ff:f8:45:e4 (RSA)
| 256 09:b9:b9:1c:e0:bf:0e:1c:6f:7f:fe:8e:5f:20:1b:ce (ECDSA)
|_ 256 a5:68:2b:22:5f:98:4a:62:21:3d:a2:e2:c5:a9:f7:c2 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.80%E=4%D=5/29%OT=22%CT=1%CU=32267%PV=Y%DS=2%DC=T%G=Y%TM=5ED0A56
OS:B%P=x86_64-pc-linux-gnu)SEQ(SP=106%GCD=1%ISR=10A%TI=Z%TS=B)SEQ(SP=EC%GCD
OS:=1%ISR=FE%TI=Z%CI=I%II=I%TS=A)SEQ(CI=RD%TS=8)SEQ(SP=105%GCD=1%ISR=107%TI
OS:=Z%CI=I%TS=C)OPS(O1=M508ST11NW6%O2=M508ST11NW6%O3=M508NNT11NW6%O4=M508ST
OS:11NW6%O5=M508ST11NW6%O6=M508ST11)WIN(W1=68DF%W2=68DF%W3=68DF%W4=68DF%W5=
OS:68DF%W6=68DF)ECN(R=Y%DF=Y%T=40%W=6903%O=M508NNSNW6%CC=Y%Q=)T1(R=Y%DF=Y%T
OS:=40%S=O%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R
OS:%O=%RD=0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=
OS:40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0
OS:%Q=)U1(R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R
OS:=Y%DFI=N%T=40%CD=S)
Network Distance: 2 hops
Service Info: Host: BASIC2; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: 1h20m03s, deviation: 2h18m35s, median: 2s
|_nbstat: NetBIOS name: BASIC2, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
| Computer name: basic2
| NetBIOS computer name: BASIC2\x00
| Domain name: \x00
| FQDN: basic2
|_ System time: 2020-05-29T02:02:00-04:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2020-05-29T06:02:01
|_ start_date: N/A
TRACEROUTE (using port 993/tcp)
HOP RTT ADDRESS
1 242.08 ms 10.9.0.1
2 242.12 ms 10.10.252.119
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap did: 1 IP address (1 host up) scanned in 90.66 seconds
We got some open ports SSH 22, HTTP 80, SMB 139
now we know that port 80 is open so we checked for the webpage but we didn't find anything interesting. So now we will run Gobuster to see if there is any hidden directory.
So we have found a directory named development so let's check the webpage.
We can see there are text files present on the webpage dev and j.txt let's try to open the text file.
So we opened both text files in dev we can see the message is about some apache struts and version 2.5.12 and the j.txt file is telling about the directory with a password in hash inside the machine. So now let's think about Apache struts 2.5.12 version we googled about Apache struts 2.15.12 to find some vulnerability and we got a Metasploit module to exploit but after trying that didn't give me a connection.
we can't get a reverse shell from the Metasploit module.
Now let's go back on Nmap script the results shows that we have SMB port open and also we have SMB version let's google if some vulnerability is there for the SMB version.
After some research we got Enum4linux- Enum4linux is a tool for enumerating information from Windows and Samba systems.
so now we can run the command "Enum4linux -a ipaddress"
After some time we found two usernames "Jan" and "kay".
Now we have Usernames so now we can Bruteforce for Passwords with Hydra tool.
Now we found Password for "Jan" now we can try to login through SSH.
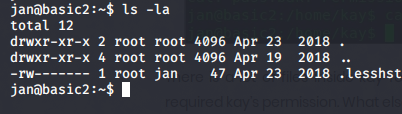
We have Successfully logged in as "Jan".Now we can check for the directories
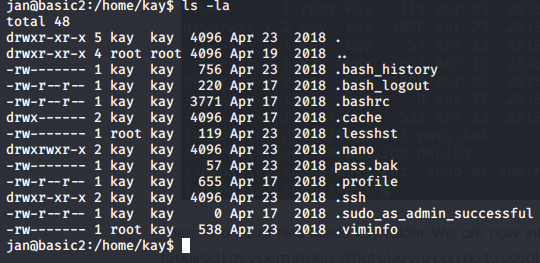
We didn't found much information after changing the directory to home we got another user's directory "kay".let's check kay's directory.
In kay's directory, we found a file ".ssh" and there was "id_rsa"
id_rsa is An SSH key is another way to identify yourself that doesn't require you to enter your username and password every time. Let's open 'id_rsa'.
After searching on google we know that this SSH key can be cracked with John the ripper. So let's try to crack the SSH key.
So first we have to locate the ssh2john.py to convert the hash and copy and save the "id_rsa" file content to our computer as a text file and we have to convert the text file into the hash format you can use the command as shown in the below image.
We got the password for Jan it took a lot of time to get the password. Now we can try to login as "kay" from "Jan" by this command
"ssh -i /home/kay/.ssh/id_rsa kay@10.10.10.10"We have successfully logged in as "kay". Now we can check the directories of "kay"
Now we can see the pass.bak file because when we were in "Jan" we didn't have the permission to view that file only "kay" has the permission. so now we can see file using this command "cat pass.bak".
Now we have the flag but we don't have root access so we have to do privilege escalation so to check what permission do "kay" have you can give this command
"Sudo -l".
Now we can see kay can access all the Sudo command.so now we are using "Sudo su" command the sudo su command will invoke as root.
Now you have successfully rooted this machine!






















2 Comments
Awsm postt❣️❣️
ReplyDeleteThank you for the walkthrough, nice post
ReplyDelete